Visualize your risk
Frame. Assess. Monitor. Respond.
CYBERLEDGER SCORE
Cyber Maturity
SOLUTION OVERVIEW
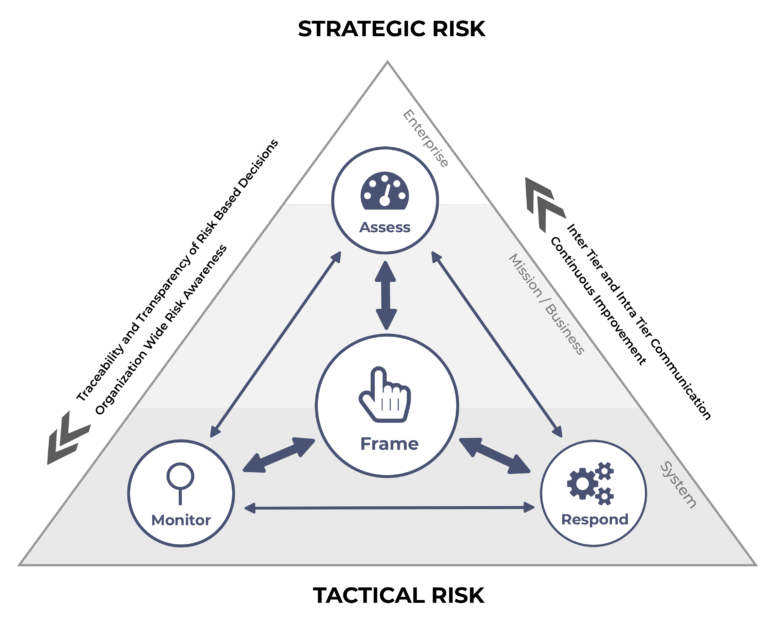
Cyberledger on a foundation of leading industry cybersecurity guidelines such as, NIST Special Publication 800-30 Guide for Conducting Risk Assessment and SP 800-37 Guide for Applying the Risk Management Framework to Federal Information Systems.
The solution employs a top-down and bottom-up approach that fully integrates risk management into every aspect of the organization and addresses risk-related concerns at:
- the enterprise or organization level
- the mission and business process level
- and other information system or component level
FRAME
System Profile
Define users, organizational tiers, system boundaries, security categorization and applicable overlays.
Risk Profile
Quantify valuation of assets to the organization and enterprise with a dynamic Risk Profile designed to use criteria that define core mission areas (e.g. Continuity of Operations, Use of Asset, Financial Implications, and Public Trust.)
Threat Profile
Automated ingests of threat data to evaluate how susceptible a system, organization and entrprise may be to a threat by cataloging attack patterns, comprehensive schema and classification taxonomy.
ASSESS
Security Control Adherence
Baseline data from Security Assessment Reports (SARs) builds the foundation to analyze and evaluate compliance gaps
Evaluate Assessment Data Quality
The import process validates if the uploaded SAR file includes the minimum baseline security controls based on the Confidentiality, Integrity and Availability security categorization rating and security control overlays
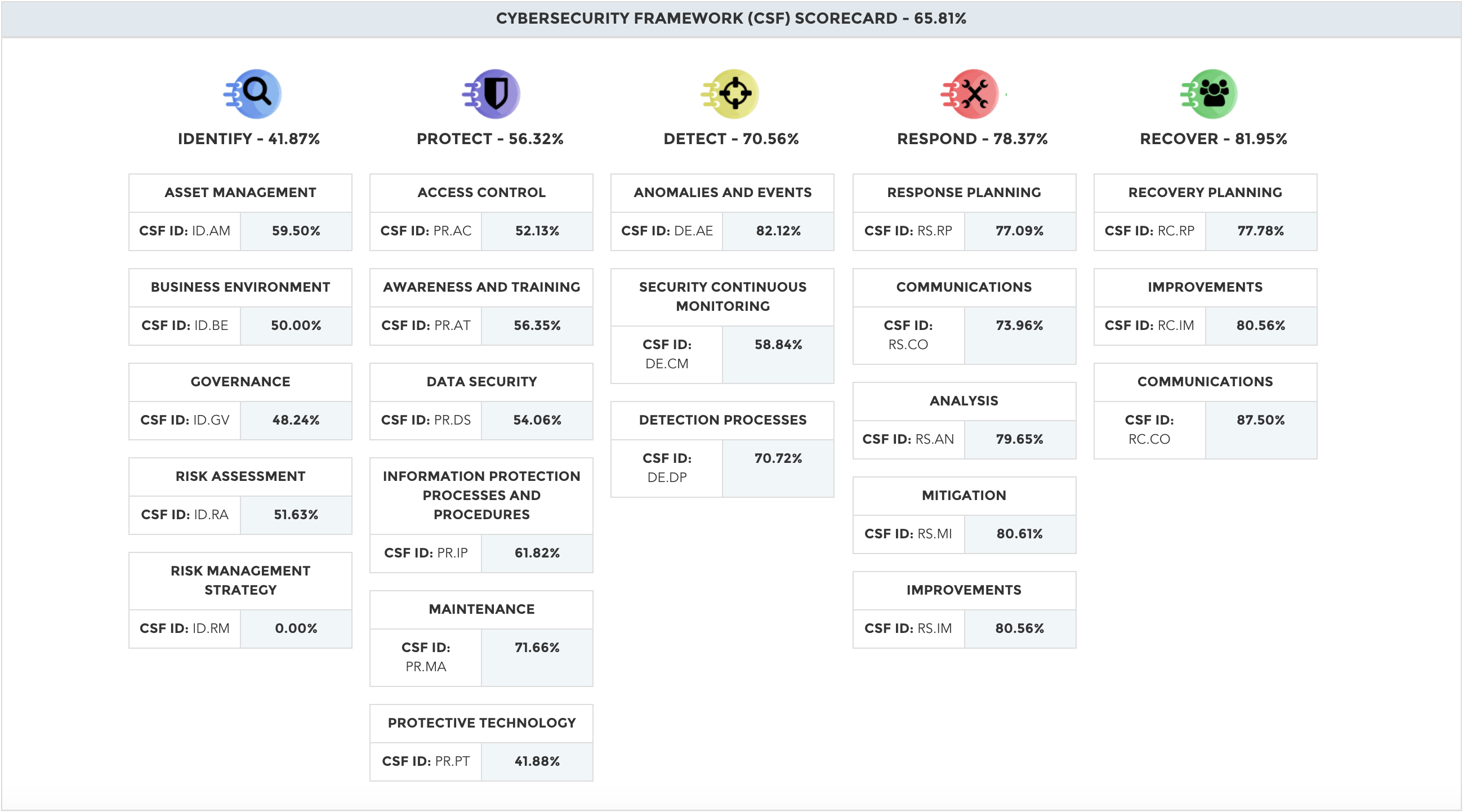
Cybersecurity Framework
Automated calculation and measurement of Cybersecurity Framework (CSF) functions, categories and control objectives using validated security assessment data.
MONITOR
Residual Risks
Examine open risk across an enterprise, organization, and system using data driven analysis, data correlation, and automated reporting mechanisms
Quantify Security Compliance
Security control compliance scoring with security control implementation details at the most granular Control Correlation Identifier (CCI) level or NIST 800-53A "Determine If Statement"
Quantify and Measure Security Maturity
Security maturity scoring with level progress and compliance improvement target trends.
RESPOND
Cost and Compliance Trending
Respond to compliance improvements across the enterprise, trends over time and anticipated cost for future budget periods.
Spending Prioritization
Prioritize the remediation of enterprise system vulnerabilities based on mission impact, threat susceptibility, available solutions and cost.
CSF Budget Plan
Generate a budget plan that maps planned expenditures to the CSF functional reporting areas. Respond to capital planning investment control (CPIC) requests and further justify/support risk based decision analysis.
solution characteristics
CYBERLEDGER is used by industry partners and customers as a cyber security(IA) services quality assurance and projects performance tool to:
- Identify and report on how well security funds are being spent
- Understand current security posture and roadmaps for archiving target security goals
- Provide management with a vision, and clear indicator of how well our cybersecurity services are improving security posture
PRODUCT
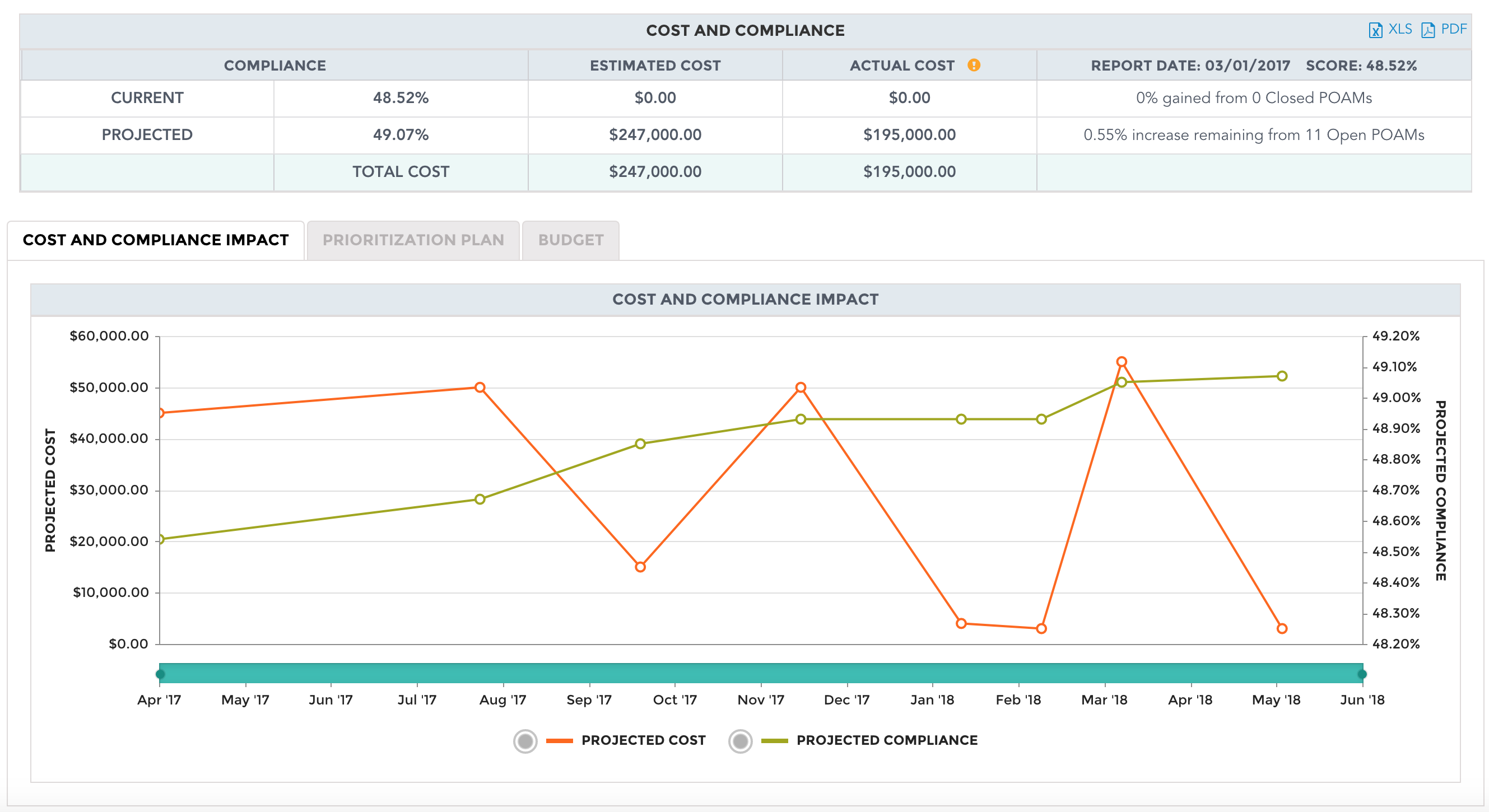
Cost and compliance
Automate the analysis of risk reduction spending prioritization plans
Calculate cybersecurity costs to close compliance gaps in systems and risk mitigation trends by cost. Saves time and cost to perform manual analysis and cost reconciliation from various cyber, operations, and financial spreadsheets.
CYBERSECURITY FRAMEWORK
Automate CSF Profiles for Reporting
Map internal goals to CSF profiles and track remediation progress to CSF profile improvement targets
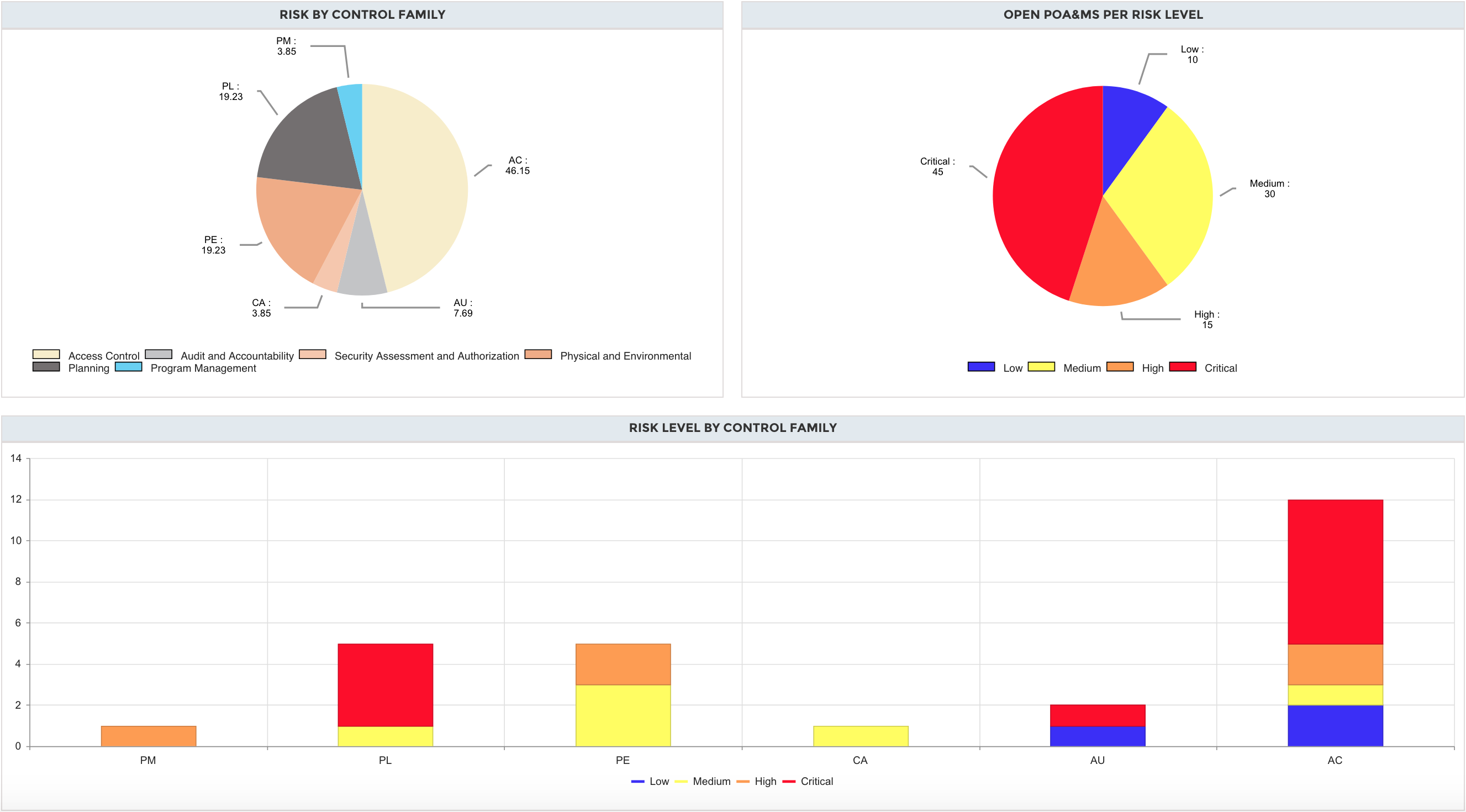
Residual risk
Automate Residual Risk Progress Tracking
Visualizes residual risk POAM activity from security assessment details for each system.
- Email: support@cyberledger.com
